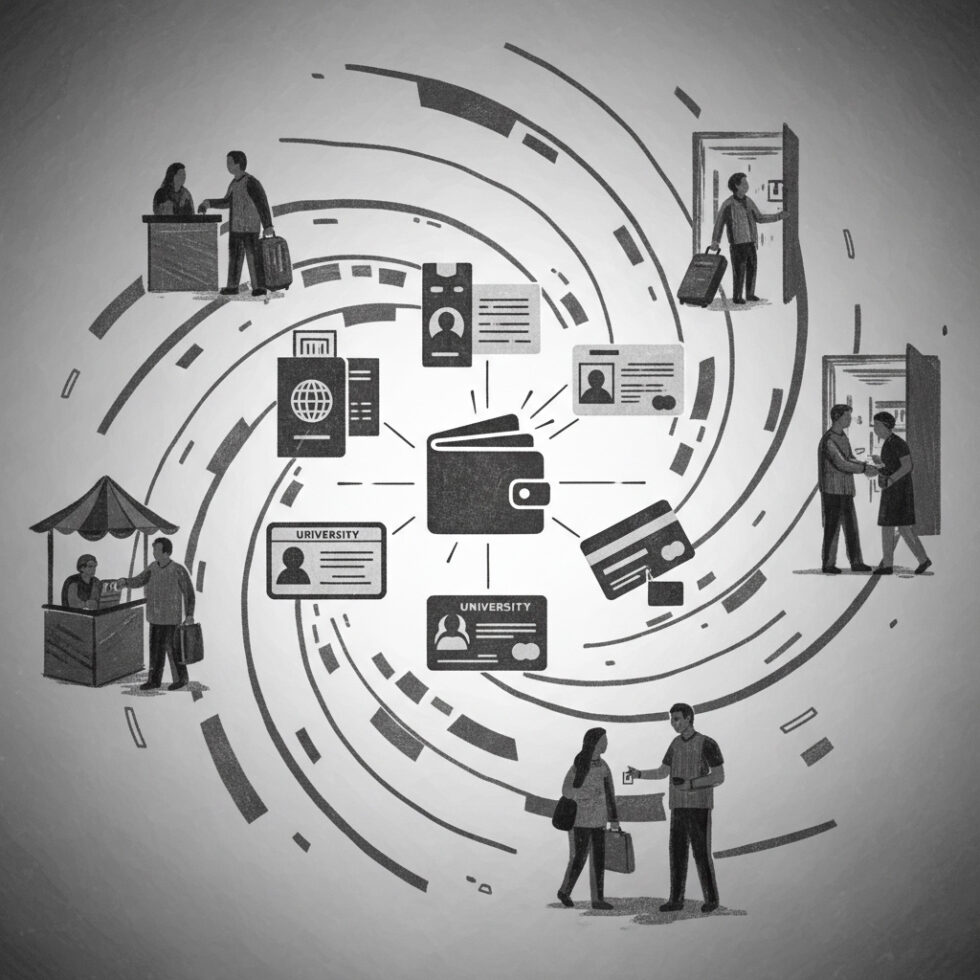
What “verifiable” really means
When someone asks you to prove who you are, you reach for a document: a driver’s license, a student card, a membership pass, a certificate. In the digital world, we mostly send copies. PDFs, screenshots, or database lookups do the job—often with too much data shared and too little trust. Verifiable credentials (VCs) change this pattern. They are digital attestations you can store in an identity wallet on your phone or laptop and present to anyone who needs to verify a fact about you.
Here’s the core idea in plain language:
- An issuer creates a credential (for example, “Pat is over 18” or “Taylor is a licensed nurse”).
- You, the holder, keep it in a secure wallet on your device.
- A verifier (a bar, a hospital, a website) asks for proof of a specific claim.
- You share a cryptographic proof, not a raw document, and the verifier can check it without calling the issuer.
The proof is verifiable because it’s signed by the issuer’s digital key. It’s private because you can often share only the information requested—sometimes even proving a statement like “over 18” without revealing your birthdate. And it’s portable across apps and borders, because the ecosystem uses open standards.
Why this is taking off now
Several trends are converging:
- Mobile-first services: More interactions—renting cars, onboarding to financial apps, entering secure workplaces—start on a phone.
- Regulation and compliance: Industries need consistent, auditable ways to check identity and eligibility without hoarding personal data.
- Open standards: The W3C Verifiable Credentials and Decentralized Identifiers specifications, OpenID for Verifiable Credential Issuance, and ISO mobile driver’s license guidelines give everyone a common playbook.
- Privacy expectations: People want to share less, not more. Selective disclosure and zero‑knowledge proofs match that demand.
Put simply: we have the need, the math, and the standards to make digital proof as convenient as tapping your card and as private as showing only the back of your driver’s license with everything but your photo covered.
The moving parts, explained without jargon
Issuers, holders, verifiers
Think of issuers as trusted sources of facts. A university issues degrees, a government issues identity attributes, an employer issues role badges. You receive those in your wallet. Later, when a verifier asks for proof, your wallet assembles a response tailored to the request.
Keys and signatures
Each credential is signed by the issuer. When you present it, the verifier checks the signature against a public key. The mechanic is similar to how browsers confirm a website certificate—automatic and fast. You don’t need to babysit keys yourself; the wallet handles that in the background.
DIDs and registries
Many systems use Decentralized Identifiers (DIDs). A DID is a stable identifier (like “did:example:123…”) that can be resolved to public keys and service endpoints. The point is not to make everything “blockchain”—many DID methods use simple registries or networks. The benefit is portability and vendor neutrality: your credential doesn’t depend on any single company’s database.
Selective disclosure
Instead of dumping an entire ID card, wallets can share only needed fields. Modern schemes can prove a statement like “older than 21” or “belongs to ACME Corp” without showing your exact birthdate or employee number. This “just enough” model trims data risk for everyone.
What this looks like in real life
Travel and mobility
You reserve a car from your phone at midnight. The rental app asks your wallet for three things: that you are over 25, that your driver’s license is valid, and that your identity matches your payment profile. Your wallet combines proofs from a government-issued mobile license and your payments provider. The agent at the desk never sees your exact birthdate or your full license number—only the confirmations needed to hand over the keys.
Hiring and onboarding
During hiring, a firm needs proof of education, right-to-work status, and license validity for regulated roles. Instead of emailing PDFs and waiting on manual checks, candidates share verifiable credentials from the source. The company’s system verifies them in seconds and stores proof of verification, not the raw documents. This reduces fraud and simplifies audits.
Healthcare check-in
At a clinic, you present insurance eligibility and consent statements. A tap or QR scan from your phone sends signed facts to the clinic’s system. The clinic trusts them because they are issued by your insurer and signed by you. If coverage changes, your insurer updates the credential, and your wallet reflects the new status automatically.
Age-gated purchases, done safely
In many regions, retailers must check age for certain products. A verifiable credential can confirm age without exposing your full identity. The retailer gets what they need and keeps less sensitive data on file.
How it’s different from today’s logins and PDFs
- Not just a login: OAuth and SSO let you “sign in with” an account. Verifiable credentials let you prove facts from many sources, not just authenticate to a service.
- Not just a database lookup: Verifiers don’t have to call the issuer each time. They check a signature locally, which is fast and resilient.
- Not just a document: A PDF can be forged or copied; a verifiable credential is cryptographically signed and bound to you as the holder.
- Privacy built‑in: Selective disclosure means sharing less by default.
Under the hood: a simple flow
- Issuance: You authenticate to an issuer (say, your university). They create a credential (degree, date, major) and sign it. Your wallet stores it.
- Request: A verifier (employer) sends a request: “Prove degree X issued by a recognized institution.”
- Presentation: Your wallet builds a proof. It might reveal the school and degree name, but not your student ID, unless asked. It signs the presentation to confirm the proof came from you.
- Verification: The verifier checks the issuer signature and your holder binding. If both match, the claim is accepted.
This is all done in seconds with standard protocols. You see a clear consent screen each time. You can decline or limit what’s shared.
Privacy and security features that matter
Holder binding
Credentials can be tied to your cryptographic keys, making them hard to transfer or resell. If someone copies your file, they still can’t present it successfully because the proof requires your key.
Selective disclosure and ZK proofs
With the right credential formats and protocols, wallets can produce proofs that reveal only what the verifier requested. Some schemes use zero‑knowledge proofs to show a statement is true without showing the underlying data.
Device security
Wallets take advantage of secure enclaves and hardware-backed keys on your phone or laptop. If you lose the device, you can recover from a backup or reissue credentials. For high-value credentials, expect extra confirmation steps, such as biometrics.
Revocation and status checks
Issuers can mark credentials as no longer valid (for example, if a license is suspended). Verifiers can check status lists or short-lived proofs so they avoid trusting stale data.
Design choices you’ll need to make
Trust frameworks
Who gets to be an issuer? What qualifies an institution as trustworthy? Many ecosystems publish trust lists or participate in formal frameworks by sector or region. For example, a health network can maintain its own registry of approved issuers. The key is to keep the rules transparent and the lists up to date.
Identifiers and methods
You’ll see formats like DID, mDL (mobile driver’s license), and SD‑JWT (selective disclosure JSON Web Token). They are not mutually exclusive. Choose formats based on your requirements: offline verification, selective disclosure needs, regulator preferences, and what wallets and SDKs your partners support.
Online, offline, and near field
Sometimes the verifier is offline (a door reader or a booth). ISO mobile ID standards and QR/NFC presentation flows support these situations. Decide whether your use case needs fully offline verification or if near-real-time online checks are fine.
A practical blueprint for organizations
1) Start with one high-friction check
Pick a single process where identity proofing is slow or risky today. Examples: proof of age, proof of employment, proof of certification. Map what data you actually need and what you can stop collecting.
2) Choose a wallet strategy
You can let users bring their own wallet, provide a white‑label wallet, or embed wallet features into your app via SDKs. BYO wallets maximize portability. Managed wallets simplify onboarding. Either way, commit to export and portability so users aren’t trapped.
3) Pick credential formats and protocols
- For credentials: W3C VC Data Model 2.0, SD-JWT VC, or ISO mDL, depending on the domain.
- For issuance and presentation: OpenID for Verifiable Credential Issuance (OID4VCI) and OpenID for Verifiable Presentations (OID4VP) are widely supported.
- For identifiers: a DID method or legacy identifiers with a verifiable trust list.
4) Build a clear user consent flow
Users should see exactly what a verifier is asking and what will be shared. Provide a “details” toggle for the curious, and a one-tap approve for routine checks. Make revocation and history easy to find.
5) Integrate verification into your backend
Verification SDKs can validate signatures and holder binding. Store proofs and audit logs, not raw personal data. Emit alerts for failed or suspicious proofs. Respect local retention rules.
6) Plan for revocation and updates
Offer status lists or short-lived credentials for time-sensitive claims. If you’re a verifier, check status when it matters most (e.g., at entry or transaction time).
7) Test with real users
Run pilots with a small user group. Watch for confusion around consent, multi-device recovery, and “what did I just share?” Provide clear language and a help article explaining how to reset or reissue credentials.
Good UX patterns to borrow
- Plain requests: “Share proof you are over 18.” Avoid IDs and code names.
- Quick glance controls: A single screen listing each requested field with an on/off toggle where feasible.
- Live indicators: “This proof expires in 10 minutes.” Reduces over-sharing and replay risk.
- Tap and go: QR for at-a-distance, NFC for close-up readers. Keep both handy.
- Soft failure paths: If verification fails, fall back to a staff review with limited access—do not force users to restart the entire process.
Common pitfalls (and how to avoid them)
Collecting too much “just in case”
If a store needs an age check, they don’t need your full address. Design your verifier to request the minimum possible. Regulators notice and reward restraint.
Hard-coding a single vendor
Use standards so holders can use different wallets. Vendor lock‑in is tempting early but becomes a drag as the ecosystem grows.
Ignoring recovery
People lose phones. Build a recovery flow that does not expose them to account takeover. Use step‑up checks and reissuance from original issuers.
Skipping audits
Verifiable ecosystems are safer, but not magic. Keep audit logs of when you requested, presented, and verified a credential. Store proofs, not raw PII, and rotate keys on a schedule.
Where this is headed
You’ll soon see identity wallets embedded in many apps you already use. Expect governments to offer wallet-compatible credentials, from tax IDs to mobile driver’s licenses. Expect employers and schools to issue staff and student credentials. Expect more devices—door controllers, kiosks, vehicles—to accept wallet proofs with a tap or scan.
The long-term win is data minimization. Businesses confirm what they need without stockpiling sensitive information. People share less, and they understand what they’re sharing. The result is fewer breaches, faster onboarding, and cleaner compliance.
Frequently asked questions
Do I need a blockchain?
No. Some DID methods use ledgers; others use traditional registries or even DNS-like systems. Choose what meets your trust and performance needs.
Can a verifier fake a request?
Good wallets check who is asking. Presentation protocols let verifiers sign their requests so you see “Request from Example Bank” with a verified name. You can decline or restrict the response.
What if my issuer disappears?
Verifiers rely on the issuer’s keys and reputation. If an issuer shuts down, existing credentials may be unverifiable after keys expire. Critical issuers should use key escrow and succession plans. Ecosystems can migrate trust lists to new stewards when needed.
Does this replace passports or plastic driver’s licenses?
Not overnight. Mobile IDs are rolling out in stages, often alongside physical documents. Expect hybrid use for years. Over time, digital-first checks will cover more situations.
Implementation checklist for a small team
- Define a single use case: e.g., age verification for e-commerce checkout.
- Select standards: VC Data Model + OID4VCI + OID4VP + an SD-JWT or JSON-LD credential format.
- Pick a wallet approach: BYO or embedded SDK.
- Integrate verification: Validate signatures, holder binding, and status. Log proofs only.
- Ship a consent screen: Plain language, field-by-field visibility, one-tap allow.
- Pilot and learn: Test with a small group, iterate on UX and error handling.
Industry snapshots
Financial services
Account opening and KYC can be compressed from days to minutes with credentials for identity proofing, employment, and income. Lenders reduce fraud by demanding cryptographically signed attestations instead of screenshots.
Higher education
Diplomas, transcripts, and enrollment proofs become verifiable, portable, and shareable with employers and scholarship programs. Alumni keep a lifelong wallet instead of chasing registrars for copies.
Healthcare
Insurance eligibility, professional licenses, and clinical consents move into wallets. Providers automate checks while storing less sensitive data, improving compliance and patient trust.
Retail and events
Age checks, memberships, and ticketing go tap-to-verify. Fraud drops when screenshots and PDFs leave the stage.
What to watch next
- Government wallets: National and regional programs will set expectations for UX and interoperability.
- Workforce credentials: Portable badges for roles, training, and safety clearances will make contractor onboarding smoother.
- Privacy tech: Expect more mainstream support for zero‑knowledge proofs and selective disclosure across wallets.
- Device acceptance: Door readers, POS terminals, and kiosks that verify without internet will unlock new scenarios.
Summary:
- Verifiable credentials are signed, portable claims you store in a wallet and present on request.
- They reduce data sharing through selective disclosure and holder-bound proofs.
- Open standards (W3C VC, DIDs, OID4VCI/OID4VP, ISO mDL) make the ecosystem interoperable.
- Real uses include onboarding, age checks, licensing, education, and insurance eligibility.
- Start with one high-friction check, choose a wallet strategy, and design clear consent flows.
- Plan for revocation, recovery, and audits; avoid vendor lock-in by embracing standards.
- Adoption is accelerating as governments, schools, and employers issue wallet-ready credentials.





